Blockchain vs Traditional Security: Which Is Right for Your App?
In today’s digital world, ensuring your app is secure is more critical than ever. Business owners and developers always seek the best way to protect their applications and sensitive data. The debate between Blockchain and traditional security methods has become more relevant. Each approach has its own advantages and downsides, and selecting the right one has a major impact on your app’s reliability and user trust.
Blockchain technology has received attention because it is decentralized and has strong security features. It provides a transparent and immutable way to secure transactions and data, which is especially attractive for apps that need high levels of trust and transparency. However, traditional security methods have been the foundation of app security for years. Encryption, firewalls, and intrusion detection systems are all well-known techniques. These methods are simple and have been used in many cases.
Good To Read: 7+ Top Blockchain Development Trends in 2025
When walking through this labyrinth, you need to know the pros and cons of each option. Cost, scalability, performance, and regulatory requirements will determine your choice. This blog will explore these aspects to help you decide which security approach is right for your app.
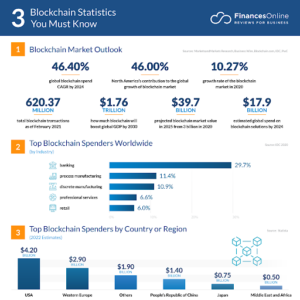
Understanding Blockchain Security
Blockchain technology uses a distributed ledger to record transactions across multiple computers. Because of this setup, it is very hard to change any recorded data without getting the consensus of the entire network. However, one of Blockchain’s biggest advantages in in-app security comes from its decentralized structure, which provides transparency and immutability.
In Blockchain, a transaction is encrypted and linked to the previous one, and together, they make a chain of blocks. It is a cryptographic method for data security, and only concerned users can make modifications. The data is spread across many nodes, so hacking at one point will not compromise the whole system.
Blockchain’s transparency means that everyone always knows what’s happening and can verify the transaction. This helps to create a greater level of trust, which is invaluable for apps that work with sensitive transactions that require high levels of trust. One of the other main benefits is that once data is written on a blockchain, it can’t be changed or deleted, making it a permanent record.
Also Read: How Blockchain will Revolutionize Industries
However, implementing Blockchain is not without challenges. Once set up, the technology can require many unique skills and be quite complex to set up and run. However, the security features are robust enough that Blockchain is an attractive choice for apps that prioritize data integrity and user trust.
Some Conventional Security Techniques
Protecting data in apps has always been the domain of traditional security methods. In most cases, these approaches are built on centrally deployed systems that are better suited for managing and controlling access. Firewalls, configuring trusted internal networks from untrusted external ones, encryption to ensure data cannot be read unless you have a key, intrusion detection systems to watch for odd behavior and much more are common techniques.
Strong authentication methods are one of the key elements of traditional security. It can be passwords, fingerprints, or two-factor authentication to verify a user’s identity. They have another critical aspect involved here: secure communication channels so that any data transmitted across the internet does not end up in an open, unencrypted place. This is done using the SSL/TLS protocols, which are widely used for this purpose (for the exchange of data, the data must pass through a secure tunnel since it can’t be transmitted openly).
However, updates and patches are crucial to maintaining the effectiveness of these security measures at a regular level. They can stay up-to-date, and new vulnerabilities can come, but they can still protect themselves from that. In addition, traditional security approaches include strict controls on user access to ensure that no one but the authorized user can access the sensitive information.
These methods are reliable, but they do need to be watched constantly. Systems are also continued to be kept secure by regular monitoring and maintenance. The ongoing effort required for traditional security techniques is well understood, and they are a dependable choice for many applications.
Evaluating Cost Factors
Blockchain and traditional security methods have different financial considerations regarding costs.
- Blockchain security can be expensive to set up at first, as it’s complex and requires professionals. That said, creating and operating a secure blockchain system requires specialized knowledge, which can make it less cost-effective to get started.
- Traditional security has its costs as well. To sustain security measures, businesses have to spend on hardware, software updates, and people. The cost can be ongoing and add to the cost through regular updates, monitoring, and troubleshooting.
- Another thing to consider is potential long-term savings. Decentralizing Blockchain can lower the cost of centralized management and middlemen. An example here would be that smart contracts can automate a process and save labor and errors in the future, saving you money.
- However, on the flip side, traditional security methods are usually easier to implement and maintain and less costly upfront. Conventional methods are less scalable or carry high costs; some businesses need help pursuing this method. In many cases they have an easier time with traditional methods.
You need to decide what trade-off fits your business, what the balance is between setup costs now vs. ongoing costs now vs. potential savings now. The choice of each method will have its own financial implications and will depend on your business needs and budget.
Addressing Scalability Issues
When your app gets more users and data, scalability is important. Taking a scalability approach, Blockchain uses partitions (sharding) and even off chain transactions (moving part of the Blockchain to a different network and sometimes reducing the burden on the main chain). However, these methods are effective, but add complexity that might otherwise not be needed and can necessitate skills that are tough to acquire.
On the other hand, traditional security solutions usually scale through simpler means. Optimizing server infrastructure and employing load balancing provide techniques that can distribute data and traffic more evenly to more than one server. This ensures that your app can scale as you grow and won’t impact performance.
Blockchain’s advanced techniques can be robustly secure, but can slow down as the network grows, and both approaches have their pros and cons. Traditional methods are easier to implement and maintain, and provide a more predictable performance as demands increase. Ultimately, the decision between these two will be based on what your app needs and how much expertise you have. Knowing how each method scales will allow you to predict your app’s growth and make sure it stays secure and efficient as it grows.
Read More: Top Blockchain Platforms for the Enterprise
Simplicity of Deployment
Blockchain security deployment can be a tough task. This requires an in-depth understanding of decentralized networks and possesses special ability. This requires careful planning; you need to set up nodes, establish consensus mechanisms, and ensure the ledger is intact. Integrating Blockchain into an already existing app is difficult and often requires major changes to both the app and the blockchain system.
On the other hand, traditional security methods typically provide a better deployment path. It makes sense to create security features like firewalls, encryption, and intrusion detection systems with established protocols and a wealth of tools to follow. These methods have well-documented processes and a wealth of resources and support to help you implement them.
Traditional security methods are familiar and accessible, making deployment quicker and less stressful for many developers. Additionally, there’s a larger pool of professionals trained in traditional security, so you’ll have a larger pool of people to choose from.
Blockchain deployment is not easy, but it has many security features. Implementing them could be easier, but it wouldn’t be easy to keep them running forever. As you gain insight into these differences, you’re able to select a security solution that supports the simplicity you’d like to achieve with undesirability and still be strategically effective.
Confused about the best security approach for your app? Hire Dedicated Developers from Hidden Brains to craft custom, secure solutions tailored to your needs!
Effects on Performance
The time taken to validate and add transactions to the ledger can influence how your app works because of Blockchain. Security comes at the cost of speed, and this process, called consensus, slows down operations as the network grows. Reliance on very fast transaction speed could be an issue if your app.
These delays are different from traditional security methods. Encryption and firewalls run quickly, so your app doesn’t slow down much. This major advantage can be achieved if real-time performance or instantaneous transactions are required.
But you want to weigh the performance drop against the security win. If your app needs high trust and transparency, Blockchain provides robust security, which can be very useful. On the other hand, traditional methods offer a nice trade-off between speed and protection for many applications.
You will have to choose between these methods based on your app’s needs. If speed is your top priority, traditional security may be the way to go. If you need the extra security and transparency of Blockchain but can live with the performance trade-off, then that might be fine.
Building User Confidence and Clarity
Blockchain’s transparency is a unique way to build user trust. It gives a feeling of security and reliability by allowing the users to verify transactions independently. Unlike the other apps we looked at, this transparency is especially valuable for apps that handle sensitive information or financial transactions, where no cheating at monitoring is tolerated. It is good to know that the users can’t mess with or alter the data.
However, traditional security methods also have ways of building trust. The app is secure because it relies on established protocols and certifications to prove it. For instance, many people know what SSL/TLS certificates are, which indicate a secure connection. The methods here are about keeping data private and secure while keeping the underlying processes hidden.
Users are more comfortable with the systems they know. Encryption and two-factor authentication are well-known and trusted by the general public. It’s a simple way to reassure users that their data is secure.
Users may need some education to fully understand the benefits of Blockchain. However, once users know how Blockchain works, the level of trust can be much higher. Both methods have their uses. How you want to balance transparency and user familiarity will determine which one you choose for your app. Each method can effectively build user confidence in its own way.
Adhering to Regulations
Any app needs to adhere to regulations, and Blockchain and traditional security methods have different ways of complying. With a blockchain, there is the opportunity to take advantage of its unchangeable record of the transactions, which can be utilized for audits and for regulatory checks. Proving this can simplify compliance with data integrity standards. However, Blockchain’s decentralized nature also has drawbacks. This technology is still catching up with regulatory bodies and there are no clear guidelines, which can create uncertainties.
Regulators are still generally more familiar with traditional security methods and are much easier to adapt to existing laws. Standard practices include encryption, access controls, and regular auditors. The methods can be adapted to meet specific regulatory requirements, making it easier to show compliance.
For example, healthcare apps must comply with HIPAA, and financial apps must comply with GDPR. Businesses have a clear path to follow with traditional security systems, which have a track record of meeting these standards.
Knowing the regulatory landscape and how each security method fits into it will help you decide which method is right for your app. This will guarantee that you meet all the requirements and that your app is secure.
Ensuring Your App’s Longevity
The right security method can make or break your app in the long run, and Blockchain, with its decentralized and immutable nature, provides a future-proof solution that can adapt to new technology and evolving threats. With the ever-increasing sophistication of cyber threats, the advanced features of Blockchain give a strong backbone to the strong defense, thereby supporting long-term security.
Traditional security methods are effective but are prone to updates and reconfigurations due to new vulnerabilities constantly emerging. However, their well-established protocols and ease of integration make it easy to adapt to new challenges as they arise. Given their quick introduction and use of known practices, they are a trusted selection for numerous applications.
Blockchain and traditional security have their own merits when it comes to app longevity. Blockchain is a new way of doing things that is always changing, while traditional methods are proven and can be updated as needed. Depending on your needs and how you see your app growing in the future, you will have to make a choice.
Security Threats and Difficulties
As Blockchain and traditional security methods have their own challenges and potential threats, both continue their operations. One of the things Blockchain is praised for is that it is decentralized, making it harder for attackers to compromise the entire system. But it comes with its risks. A 51% attack, which happens when a single entity controls more than half the computing network power, is one major threat since that entity could modify the ledger. Privacy vulnerabilities in smart contracts can also be exploited, and given the huge sums of money that can be exchanged between users via a smart contract, this can lead to security breaches and loss of funds.
Phishing, malware, insider attacks and other existing threats continue to plague traditional security systems. Phishing schemes run off users by persuading them to hand over sensitive information, and malware compromises systems, and wreaks havoc. The other large problem is that of insider threats, where people abuse their rights and misuse their in-house ability to look at private information. Maintenance for these systems is constant updates and monitoring to keep up with ever changing threats.
Both have to be carefully managed and mitigate risks. Blockchain is complex to secure, and traditional methods require a close eye on emerging vulnerabilities. These difficulties help you understand the best security method to protect your app and its users. Working towards such robust security is crucial— our awareness of the potential threats.
Personalization and Adaptability
Smart contracts are a high degree of personalization that blockchain technology provides. These self-executing contracts can be fine-tuned to hard-enforce rules and conditions specific to your app. That means you can create custom security measures that are perfect for your app. For instance, a financial app can implement smart contracts that will automatically carry out transactions only when some defined conditions are met, securing and increasing the level of accuracy versus pure manual transactions.
At the same time, traditional security methods are also very flexible. Most traditional solutions have modular designs, and they can be configured to fit the specific needs of your app. For instance, you can implement various amounts of encryption, different authentication methods, setting a control based on user role, etc. This flexibility can help you create a security framework that matches your app’s features and user interactions.
Both approaches provide some customization options. Traditional methods provide tried-and-true solutions that can be easily adjusted, while Blockchain provides a modern, programmable layer of security. Depending on the app’s security requirements, you can choose the option that fits your app’s needs.
Examples and Case Studies from the Real World
There are many apps that show the strengths of both Blockchain and traditional security methods. For instance, transactions between Bitcoin or Ethereum prove to use Blockchain for secure, transparent transactions. These platforms build on these implementations by leveraging these decentralized ledgers to build trust and avoid fraud; hence, they are pioneers in blockchain adoption.
- IBM’s Food Trust, a blockchain solution employed by big name retailers such as Walmart to trace the sources of what we eat as a way to assure safety and transparency in the supply chain.
- On the traditional security side, banking apps like Chase and Bank of America use only advanced encryption and multi-factor authentication to protect users. These apps use well established security protocols to protect customer information from being breached.
- Like e-commerce giants like Amazon, whose user payment details and personal information are protected using traditional security measures like SSL/TLS, traditional security measures are also used by organizations like Amazon.
Each approach has worked in its own scenario. Blockchain brings new solutions to industries that require high transparency and security, while traditional methods offer reliable, scalable protection for a broad range of applications. These are real world examples of how each method can be successfully applied to meet a particular security need.
Facing challenges with app security and trust? Empower your app with our Blockchain Development Services today.
Choosing the Appropriate Strategy
Choosing the best security strategy for your apps is dependent on many key factors.
- First, look at your app’s nature and what kind of data it works with. Because it’s immutable and transparent, blockchain can also be an advantage if your app involves processing highly sensitive information such as financial transactions or personal data. A strong contestant for applications that require the highest level of security, such as apps where trust and data integrity play an important role, its decentralized structure provides a high level of security.
- However, if your app must scale fast and process an enormous number of transactions in real time, traditional security methods may be better. These approaches are easier to implement and maintain, therefore quicker to deploy and easier for users to experience. Established methods such as encryption and firewalls can provide solid protection and very good performance.
- Look at your technical trick. Setting up and maintaining a blockchain will require some specialized skills, which means that your initial costs may be higher and the learning curve might be steeper. However, the pool of knowledgeable professionals for traditional security is richer, so that pool is easier to tap into when you need it.
Consider also compliance with regulatory requirements. Sometimes, regulators are better able to understand traditional methods, and it can be easier to get in sync with existing laws. But Blockchain can also be used to meet certain standards because it allows for an unchangeable audit trail. Weighing these factors will allow you to pick a security strategy that best suits your app’s goals and needs.
Wrap-Up and Final Thoughts
The choice of security method for your app is important. It’s richly secured due to its decentralized and transparent nature and is best suited for apps that have high trust, and want high data integrity. But, encryption and firewalls, which offer more reliable security, are easier to implement and manage, and are well suited to many applications. Then, think about your specific app details, such as cost, scalability, and regulatory needs, to decide. There are strengths to each method, and they can all help your app succeed. Weighing these factors will help you to keep your app secure and trusted by users.







Leave a Comment